Middle man attack attacker security network excited secret know who software development tutorials tutorial Middle man attack security men protect ask software better questions these dangerous why Middle man attack class superfish lawyers threats conversation stealthy cybersecurity action using abovethelaw
Man in the Middle Attack: Tutorial & Examples | Veracode
Man middle attack computer security perpetrated 1: example of man in the middle attack on a simplified version of our What is man in the middle attack?
Man in the middle attack: tutorial & examples
Man-in-the-middle attack (mitm)Attack middle man arp spoofing attacks mac wifi cyber public explained adware data attacker performing network just security but executing Man-in-the-middle attacks explained, definedAsk these 9 security questions to better protect your software.
Man-in-middle attack – what you need to know? – secudemy.comWhat is a man-in-the-middle attack Middle man attack hacker hacking mitm attacks prevent cyber hackers executing find real steps minutes just computer work hack peopleAngriff mitm roxane suau.

Prevention prevent mitm vpn
Middle man attack why migration securing site longer option mainstreethost switch makeWhat is man in the middle attack in cyber security? Man-in-the-middle attack: definition, examples, preventionExplained hackers eavesdrop whatismyipaddress.
Mitm ataque attaque kaspersky milieu atak angriff need prevention ist secudemy gegen verteidigen លហ gamebrott tecnicasSecuring your site: why https migration is no longer an option Middle man attack prevent doAttack software.

Man in the middle attack: tutorial & examples
Middle man attack mitm ionos patterns digitalguide techniquesMiddle man attack samsung insights featured posts attacks Attack middle man mitm network example wifi ip attacker arp geeksforgeeks does3 ways to mitigate man-in-the-middle attacks.
Attack middle man cyber askcybersecurity dvorak michelleSimplified version swip 10 steps to prevent man in the middle attacksWhat is a man-in-the-middle cyber attack?.

Stealthy cybersecurity threats: a conversation with the superfish class
Man-in-the-middle attackExecuting a man-in-the-middle attack in just 15 minutes Mitm examples network veracode intercepting scenario attackerWhat is a man-in-the-middle-attack (mitm) and how to protect yourself.
Mitm attacksMan in the middle attack What is a man-in-the-middle attack? how do you prevent one?Computer security and pgp: what is a man-in-the-middle attack.

Middle man attack attacks mitm tutorial arp poisoning
Attack middle man mitm example security application may when mezquita ty posted .
.
 Attack.jpg)

Man-in-the-Middle Attack: Definition, Examples, Prevention

Stealthy Cybersecurity Threats: A Conversation With The Superfish Class

Ask These 9 Security Questions to Better Protect Your Software

Securing Your Site: Why HTTPS Migration Is No Longer An Option

What is a Man-in-the-Middle-Attack (MITM) and How to Protect Yourself
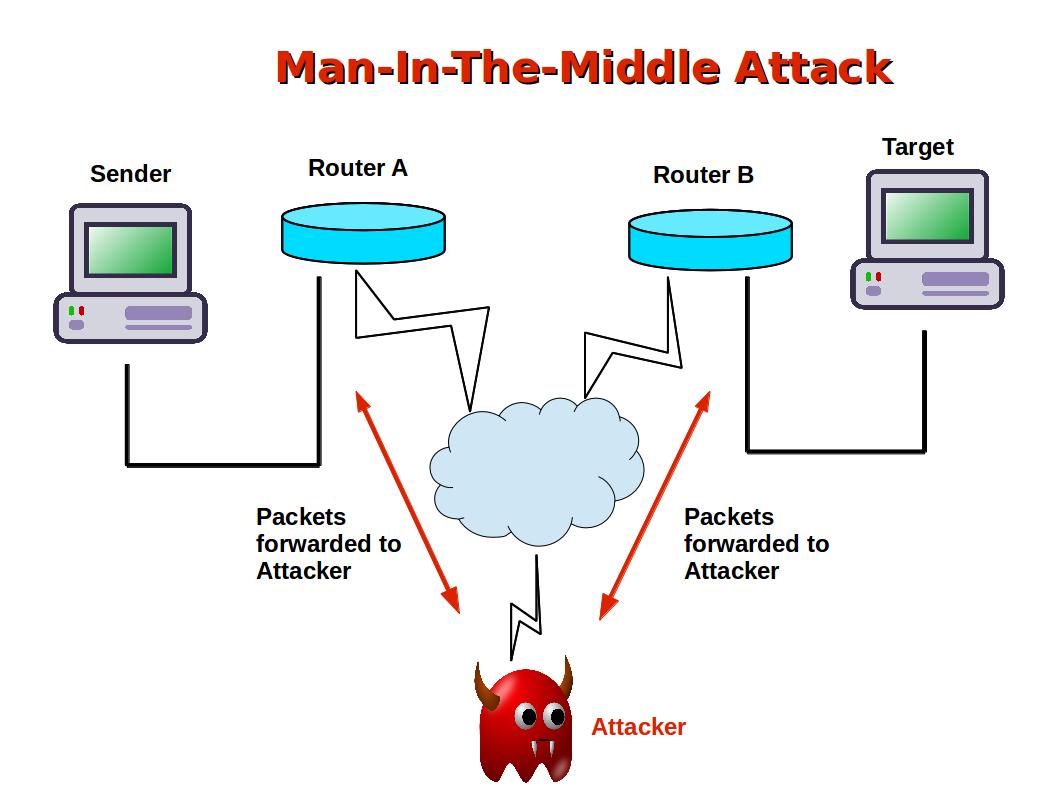
Computer Security and PGP: What is a Man-In-The-Middle Attack

Man-In-Middle Attack – What you need to know? – SecuDemy.com